Last year I wrote a Forbes article that provided a deep dive into IBM Quantum Safe solutions. That article explained how Quantum Safe protects against the future encryption-breaking power of quantum computers by simplifying the process of detecting classic cryptography. In practical terms, it enables clients to begin the process of transforming their security measures with quantum-resistant algorithms.
In this article I cover recent updates to the IBM Quantum Safe solution architecture that aim to drive the industry toward cryptographic agility—or “crypto-agility” for short. Crypto-agility provides an organization with the ability to quickly change its cryptographic methods and algorithms when new security threats or vulnerabilities are detected.
IBM Quantum Safe’s new capabilities provide network-based cryptographic inventory analysis to identify the types and locations of cryptographic instances and the relationships between assets and data flows. This allows an organization to apply (and measure the application of) cryptographic policies and generate prioritized lists of vulnerabilities. It also integrates with common ticketing systems to assist in the replacement of expired and otherwise unsuitable classical encryption schemes.
Quantum Safe Solutions
Today’s approach to public and private key cryptography is based on the mathematics of large numbers. One of our most common asymmetric encryption codes, Rivest-Shamir-Adleman, was created to ensure the confidentiality and integrity of data. RSA uses a 2,048-bit composite integer that is the product of two very large prime numbers. RSA is virtually impossible for classical computers to break; researchers estimate it would take our most powerful classical supercomputers 300 trillion years to break it. But future quantum computers will have the computational power needed to unravel the mathematics used to produce RSA-type encryption.
If it becomes possible to decrypt important data like that and there is no form of remediation available, the consequences will be staggering. At the extreme, it could result in worldwide chaos and possibly cause the collapse of global financial systems.
Birth Of The Quantum Threat
Quantum’s threat to encryption began in 1994, when Bell Labs mathematician Peter Shor developed a quantum-based algorithm that could factor large prime numbers. When Shor’s algorithm was published, there were no quantum computers in existence. While we do of course have quantum computers today, none of them are advanced enough yet to effectively run the algorithm at scale. That said, a suitably equipped future quantum computer running Shor’s algorithm could hypothetically break RSA within a few hours.
Symmetric encryption, another form of cryptography, uses a single digital key. Although quantum can’t directly break symmetric encryption like it can with asymmetric codes, a quantum search algorithm called Grover’s algorithm can be used to perform a brute-force search for the encryption key, thus reducing the time needed for decryption of important data and information. As with Shor’s algorithm, we must assume that at some point quantum computers will be powerful enough to perform this decryption quickly enough to jeopardize computer systems that protect sensitive data.
Becoming Quantum-Safe Is A Transformational Necessity
Most IT managers want to know how long it will be until quantum computers can break classically encrypted assets. Unfortunately, there is no way to know exactly when that will happen. However, there are studies that estimate when RSA-2048 can be broken.
One study concluded RSA-2048 won’t be broken until after 2039. Another 2023 study surveyed quantum experts who collectively opined that there was a 50% probability that RSA could be broken by 2029. The National Institute of Standards and Technology weighed in several years ago with its estimate that cryptographic breaches could come as soon as 2030. Based on IBM’s combination of business experience in this area and its extensive quantum research, it believes classical encryption will likely be broken within seven to 15 years, with 10 years being the most probable.
The nature of the estimates predicting when RSA can be broken might give the misleading impression that we have plenty of time to sort this out. In fact, there is not an overabundance of time left before organizations need to prepare for a post-quantum world. Since the process will be complex and lengthy, large organizations should begin early implementation plans for a quantum-safe environment. Moving from classical to quantum-safe computing is a transformational change, which means it will take years to implement and it will fundamentally change the organization in some way. To be effective, every instance of classical encryption must be remediated in every layer of an organization’s infrastructure. And that can only be done with a methodized system like Quantum Safe.
Forthcoming New Encryption Standards, With More On The Horizon
The U.S. government has been aware of quantum’s encryption-busting capability for several decades. In 2016, NIST initiated a Post-Quantum Cryptography Standardization Process and requested nominations for public-key quantum-safe cryptographic algorithms. In response to the request, NIST received 82 submissions.
After several rounds of intense scientific evaluation, four finalists in NIST’s portfolio of algorithms are expected to become certified shortly. These are CRYSTALS-Kyber for key encapsulation, and three algorithms for digital signatures: CRYSTALS-Dilithium, FALCON and SPHINCS+. With the exception of SPHINCS+, the finalists were developed by IBM. (The developer of the fourth selection is now working for IBM Research as well.)
IBM’s three algorithms are based on lattice cryptography instead of the mathematics of large numbers used by RSA encryption. Lattice algorithms are beyond the computational reach of quantum computers. These algorithms rely on the geometry of numbers and finding the shortest vector in a high-dimensional lattice for problems such as the shortest vector problem or learning with errors. Meanwhile, SPHINCS+ is a refinement of standard hash functions.
The Department of Commerce was expected to officially announce the certification of the approved algorithms in July. Since that didn’t happen, it will likely happen sometime soon after the publication of this article. Regardless, now that the new lattice algorithms are near certification, organizations should feel comfortable to begin planning to use the certified quantum-safe algorithms to enhance susceptible classical encryption methods.
It is important to note that the industry’s first quantum-safe system, the IBM Z16, also uses lattice-based cryptography. Although it is already shipping with the Kyber and Dilithium algorithms, we can assume that at some point the Z16 will be retrofitted with the newly certified algorithms.
Despite the strength and current quantum-proof nature of lattice cryptography and improved hash functions, NIST and the entire ecosystem will continue searching for novel and stronger encryption schemes. In fact, in January 2023, NIST opened another competition for new algorithms, and by now there are 52 schemes in play.
Crypto-Agility And IBM Quantum Safe’s New Architecture
The ever-increasing diversity of future encryption technologies is another reason why crypto-agility is so important. IBM Quantum Safe was one of the first systems to address the management, monitoring and replacement of classical encryption with quantum-safe algorithms. Despite its leadership in this area, IBM recognized the need for a more agile architecture. The system needed better governance to manage cryptography, more efficient ways to consume cryptography and an automated method to simplify migration to new types of emerging cryptography technology as needed.
To achieve all of that, IBM has embraced crypto-agility and integrated it throughout Quantum Safe’s new architecture. This gives the system a robust, adaptable and future-proof approach to cryptography. It also makes migration to quantum-safe algorithms easier because it supports a mix of both classical and quantum-proof encryption.
At a high level, many of the changes to Quantum Safe are captured in the evolution of IBM’s explanatory diagrams for the system. Here is the simple version of how the company depicted it in 2023.
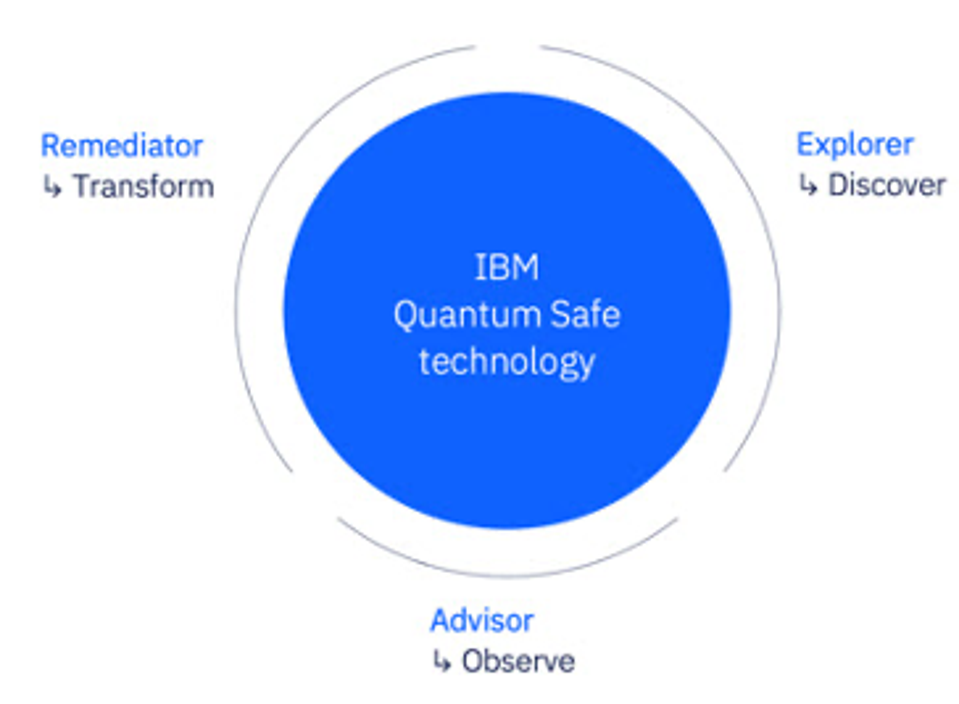
And here is the diagram depicting Quantum Safe with crypto-agility today.
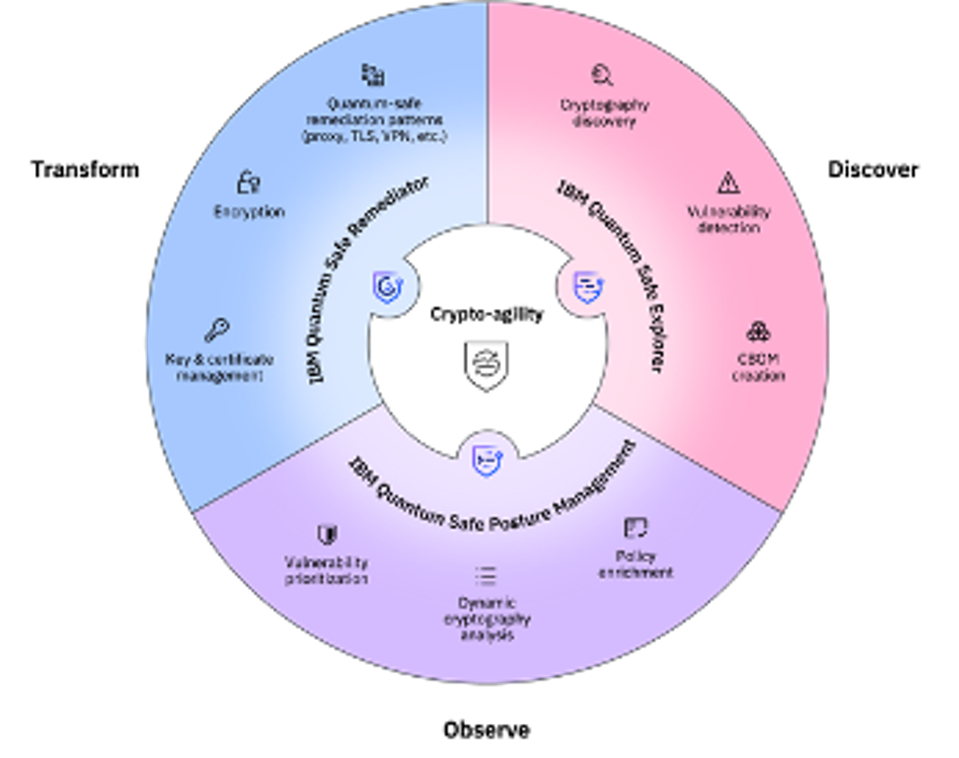
Although Quantum Safe’s core functions of discovery, observation and transformation are common to both diagrams, crypto-agility permeates 2024’s strengthened architecture. What used to be called Advisor is now called IBM Guardium Safe Posture Management, which signals IBM’s future intent. Its entire array of data management and data protection services are all now being migrated to support quantum-safe backbones.
Implementation Of Crypto-Agility
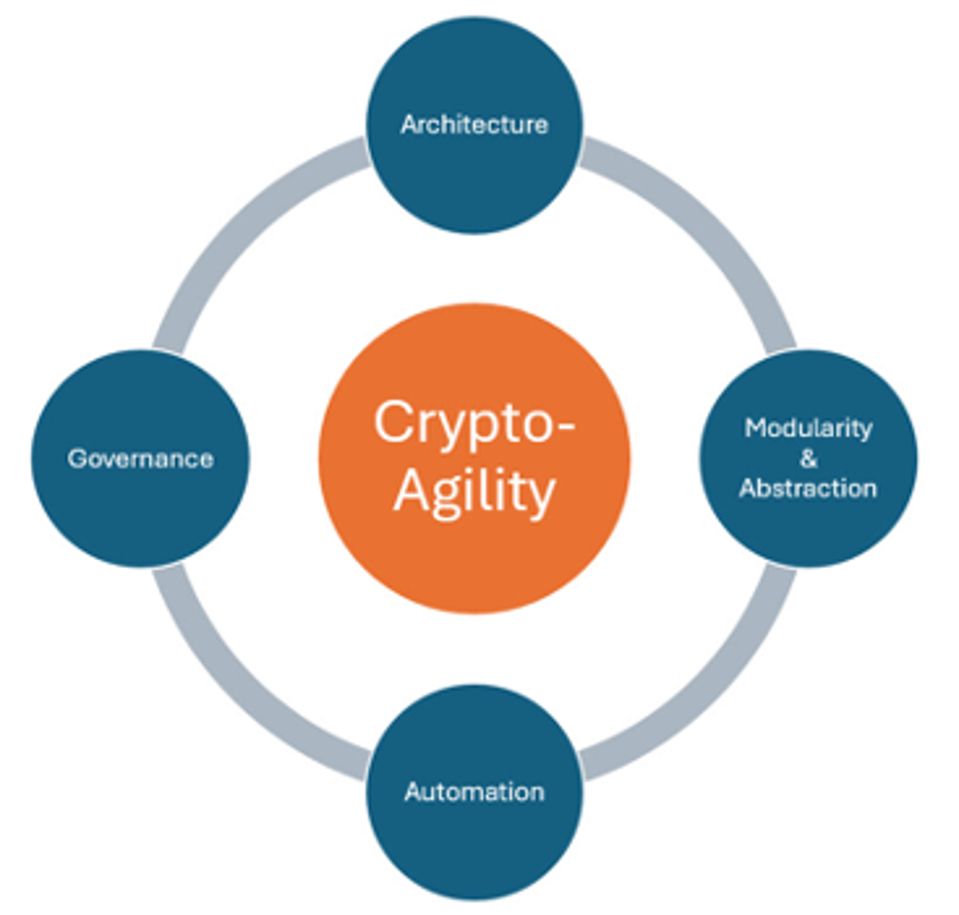
It’s important to understand that crypto-agility is not a one-time set-and-forget task, but a continuous process with interlocking parts as indicated in the diagram above. Crypto-agility strengthens an organization by augmenting its cryptographic architecture and governance with the automated controls needed to detect and correct evolving cyberthreats with minimal disruption.
The following image shows how IBM translates the different aspects of crypto-agility into a sample timeline that outlines the steps for implementing quantum-safe practices and technologies.
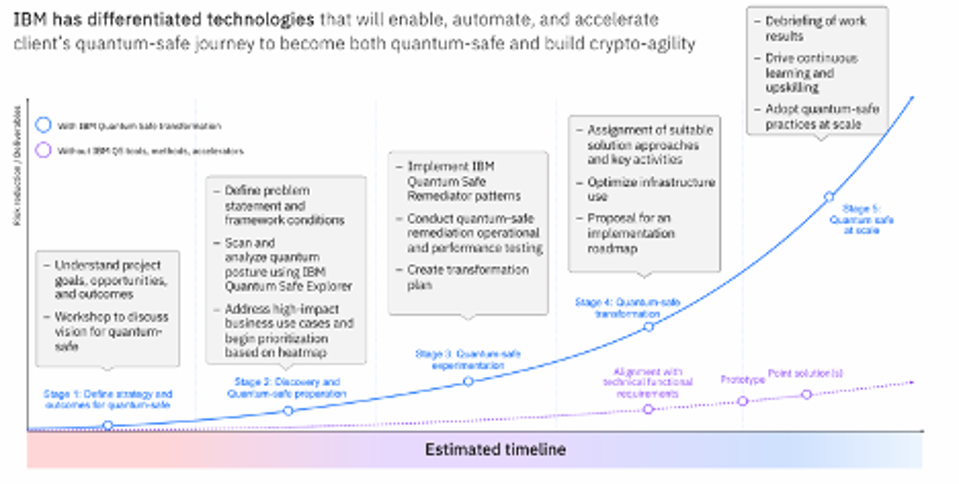
Whether you adopt IBM’s specific methodology or take some other approach, here is a list of high-level steps necessary to achieve a quantum safe environment:
- Inventory cryptography and map any dependencies across your enterprise IT landscape.
- Establish cryptographic governance within your enterprise and across the supply chain.
- Incrementally migrate to quantum-safe cryptography through code and network remediation practices.
- Get involved with quantum-safe consortia such as the Post-Quantum Cryptography Consortium and the Post-Quantum Cryptography Alliance to stay up to date on best practices for implementation.
Make Your Organization Ready For The Quantum Cryptography Era
Advancement of quantum technology is continuous, and every day we take another step closer to the time when quantum computers can crack classical encryption algorithms. But a major advantage we have is that the certified quantum-safe schemes mentioned above will soon become available—with more to come in the NIST pipeline.
Meanwhile, IBM is following its own advice. Quantum Safe has been a feature of its cloud architecture for a while, and as part of its internal process of becoming a quantum-safe organization, IBM is migrating more than 35,000 critical applications. Keep in mind that achieving quantum safety isn’t only about individual algorithms or systems; it encompasses the entire ecosystem and its software supply chain. Organizations should initiate a planning phase early—and today is not too soon—to ensure that critical applications have the necessary protection when fault-tolerant quantum computers become available.
Becoming quantum-safe is a multi-year process. Any organization that wants to avoid a future quantum-related security disaster needs a well-planned course of action to remediate every encryption artifact with a post-quantum algorithm before encryption-breaking quantum computers are developed. The time to get started is now.